If you publish WordPress themes, it’s important to develop them with the security of your users in mind. However, the WordPress Theme Review Team recently showed that many theme authors eschew this at an alarming frequency.
We understand: getting a theme and its elements to simply work is much easier than worrying about any security aspects. Even so, themes can be a huge security risk, so this is something you must concern yourself with. In fact, there are a number of security mistakes that crop up time and time again, and the good news is that fixing them in your own code is simple.
In this article, we’ll firstly discuss why security matters within WordPress themes. We’ll then introduce you to six frequent security problems, and how you can fix them. Let’s get started!
Why Basic Security Matters When Developing WordPress Themes
When we talk about poor theme security here, we mean giving hackers easy access to WordPress users’ sites. It’s surprisingly easy to build themes with huge holes in the code for ‘undesirables’ to exploit. In fact, according to the WordPress Theme Review Team report, at least half of rejected themes had security issues. It’s also worth noting 29 percent of hacked WordPress sites were accessible simply because of theme security issues.
As automation tools improve, the review team may begin implementing automatic theme checks. The easiest and fastest way to get your new themes in the directory currently is to write secure code from the start. If the system becomes automated, knowing how to do this could mean your theme goes live incredibly quickly!
To learn more about submitting successful themes, it’s worth reading the theme review process in depth. You may also want to take a look at the Theme Unit Test Data and the Theme Check plugin. Both can help you nip any issues in the bud before you submit your theme.
6 Common Security Problems in WordPress Themes and How to Fix Them
We’ll admit, it’s impossible to write code that’s 100% hacker proof. However, there are a number of known entry points and weak spots you can address to help close out the most basic of attacks.
Based on the data provided by the WordPress Theme Review team, we’ve identified six of the most common security mistakes made by developers. Learning about these will help you become a better developer overall while helping your themes to become accepted into the WordPress directory much faster.
1. Missed Data Escapes
Escaping data is one way to protect a site from SQL injection. To escape your data means to ensure that any user-provided text is processed as a string, rather than a database command. The process of cleaning data on input is called ‘sanitization’ while displaying user input requires escaping.
SQL injection is one of the most common ways to hack a site, and almost anywhere a website accepts user input (such as a post submission form, for example) can be used to hack into the database. Fortunately, WordPress core offers many ways to quickly and properly sanitize data without needing to be an expert.
Before saving any user-provided data, you can use one of the provided sanitize_* methods…
$input_email = sanitize_email( $_POST[‘email’] );
…and to display user input, you can also use the WordPress escape functions:
<h4><?php echo esc_html( $title ); ?></h4>
Just remember: sanitize before saving any user input, and escape the data before displaying it, and you’ll be good to go!
2. Using Functions Incorrectly or Reinventing the Wheel
Writing your own functions may sound like a swell idea at first, but for many situations, WordPress already offers a secure version you can use. What’s more, writing your own functions to circumvent those found in core means bypassing all of WordPress’ security measures. When possible, it’s best to use a function that has already been vetted by experienced developers.
Many theme authors attempt to recreate features such as custom logos, CSS snippets, post excerpts, and pagination. While customizing these elements is not necessarily the wrong move to make, you should learn how to properly use hooks to modify WordPress’ existing features primarily.
For example, let’s say you want a more robust excerpt feature. Rather than building your own custom function from scratch, you can simply tap into WordPress by hooking into the get_the_excerpt filter. From there, you simply tweak the output, and your theme will continue to work using the default the_excerpt() function.
Of course, writing code in this way means you’re not only making your theme more secure, you’re creating cleaner code in the process.
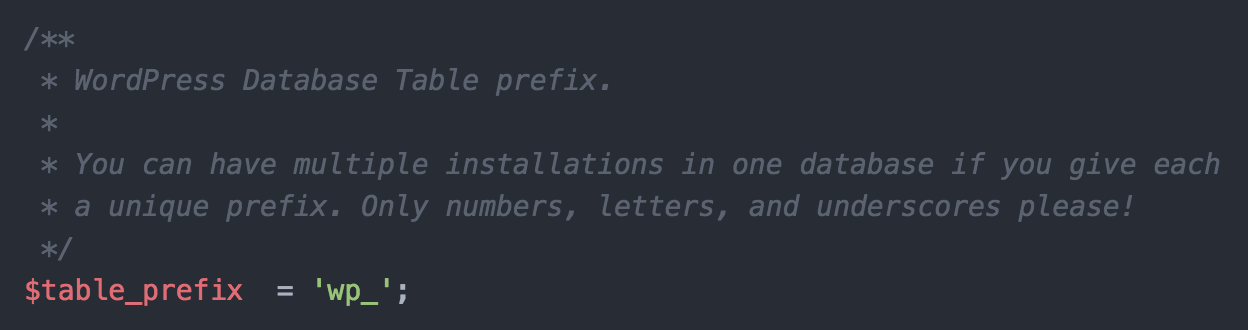
3. Not Using Database Prefixes
If your theme connects to the database using custom queries for any reason, you must use database prefixes. You can see the database prefix being set in the wp-config.php file. Note how the prefix is editable!
As with functions, not using the WordPress database prefix means your theme is bypassing all typical WordPress security measures. This removes it from the WordPress ecosystem and opens the database up to potential hacking.
This means whenever you write or read from the database with a custom query, you should make sure you’re calling the WordPress database prefix:
global $wpdb; $table_name = $wpdb->prefix . "customtable";
That way, your theme will keep to database security standards. It’s a simple implementation that could arguably have the biggest consequence to your theme’s security.
4. Skipping Enqueue Scripts
You never know when an improperly loaded script accidentally gives hackers a way to access data they shouldn’t be able to. However, for the most part, your external scripts are probably not the cause.
Even so, it’s always safest to ensure your scripts load only when they need to, and not at any other time. To do this, you’ll need to use WordPress’ enqueue functions rather than hard-coding your scripts into your theme’s header and footer. This will also ensure better compatibility with any plugin that tries to concatenate or shrink external scripts, and means your scripts will play much more nicely with others.
Here is an example of what it looks like to properly enqueue your CSS and JavaScript files in functions.php:
function themename_scripts() {
wp_enqueue_style( 'custom-style-name', get_stylesheet_uri() );
wp_enqueue_script( 'custom-script-name', get_template_directory_uri() . '/js/example.js', array(), '1.0.0', true );
}
add_action( 'wp_enqueue_scripts', 'themename_scripts' );
Learning to use the enqueue functions may feel odd at first, but it is actually very quick and easy to do once you learn. In any case, the security benefits you’ll receive are more than worth the extra effort.
5. Ignoring PHP Errors and Warnings
When something isn’t quite right in your code, you’ll an error or warning – of course, this enables you to fix it. However, it’s possible that your development environment hides these errors. This means your theme may have security issues you aren’t even aware of.
These errors and warnings may not always indicate something is strictly insecure, but it does mean your theme could easily shut down a users’ entire site after activating it. Of course, this isn’t a desirable situation to be in.
To address this, simply ensure that PHP error reporting is turned on for your local environment – and if an error or warning pops up, don’t ignore it! If possible, test your theme on the most recent two or three versions of PHP for maximum compatibility. Environments like Vagrant make this relatively simple to do.
On the whole, this is likely a step that many of you already follow, but even so, it’s worth stating again!
6. Packaging Unused Code and Files
When building a theme, you may often add in extra code or files to try and make something work temporarily. By the time you’re finished, a lot of that code could be unnecessary. In short, any code in your theme that isn’t being used increases the chance of someone exploiting it and compromising your theme’s security.
In order to avoid this, you can run your own miniature code review before submitting your theme to the WordPress directory. This means combing through your code and ensuring:
- It follows the PHP coding standards for WordPress.
- Any code that isn’t being used gets removed from the theme.
- All code is easy to understand just by scanning it.
If you run into code or files that aren’t being used at all, remove them! Again, this is another simple tip that only requires a minimal amount of effort. but has far-reaching consequences on your theme’s – and ultimately your user’s – security.
Conclusion
Being able to write secure themes helps you put out safe products with a higher approval rate in the WordPress theme directory. While you don’t need to be a security expert per se, it is important to understand the basic measures you need to take within your theme’s code.
In this post, we’ve covered six common security mistakes found in WordPress themes, and how to fix them. Let’s recap:
- Missed data escapes.
- Incorrectly used functions.
- Misusing data prefixes, or not using them at all.
- Skipping enqueue scripts.
- Ignoring PHP errors and warnings.
- Including unused code and files.
Do you have any further questions about writing secure themes? Ask us in the comments section below!
Image credits: Henry Hustava

No Comments
Start the conversation